Posts Tagged 1.0
SAMM Workshop Next Week in Hamburg
Posted by Colin Watson in Discussion on August 14th, 2013
Further to the previous announcement, the schedule for the SAMM workshop at AppSec EU in Hamburg next week has been published.
During AppSec conferences, the SAMM project team will organise workshops for you to influence the direction SAMM evolves. This is also an excellent opportunity to exchange experiences with your peers. Similar workshops will be organised in New York (USA) and Lima (Peru) in the coming months.
Next week on Wednesday the project leaders are holding the first of these OpenSAMM workshops at AppSec.eu in Hamburg:
- Location: Alster room in the Scandic Hotel, Hamburg, Germany
- Time: Wednesday August 21, 2013 1:00pm – 4:00pm
The agenda is:
- Introduction / getting to know each other – 10 mins
- Project status and goals – 10 mins
- OpenSAMM inventory of tools and templates – 20 mins
- Case studies / sharing experiences – 40 mins
- What do we need (thinking about improvements, can be anything ranging from translations over tools to model improvements) – 40 mins
- What do we need first (prioritization) – 30 mins
- Call for involvement (responsibilities), identity teams for specific topics – 15 mins
- Rough planning for the future – 15 mins
If you plan to come, can you add your name to the online meeting document.
If you would like to cover other topics, don’t hesitate to contact Seba Deleersnyder or Bart De Win.
Hopefully there will be a gotomeeting call to allow for remote participation; please let Seba or Bart know if you would like to participate remotely.
SAMM workshops at AppSec EU and AppSec USA
Posted by Colin Watson in Discussion on August 2nd, 2013
If you plan on attending http://appsec.eu or http://appsecusa.org/ be sure to get involved in the SAMM workshops (scheduled on Aug-21 and Nov-20). In Hamburg, the SAMM workshop will be on Wednesday afternoon 21-Aug, one day prior to the conference.
If you plan to attend the workshop: let us know via the project mailing list.
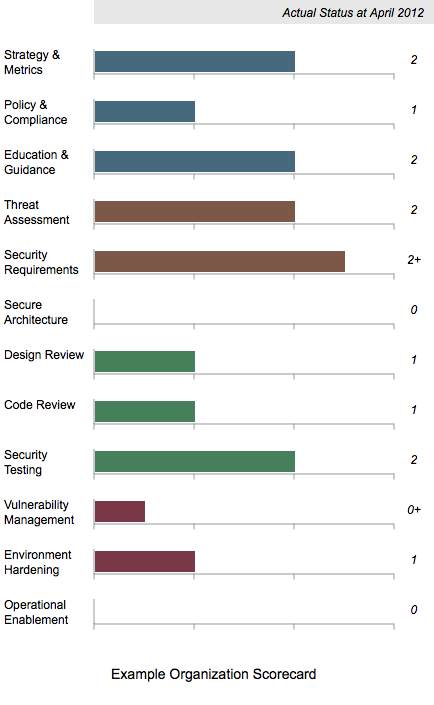
Scorecard Chart Generation
Posted by Colin Watson in Discussion on August 7th, 2012
Building on the work undertaken with Brena Larcom to create SAMM roadmap charts (Part 1, Part 2 and Part 3), I have developed a similar process for single point in time scorecards.
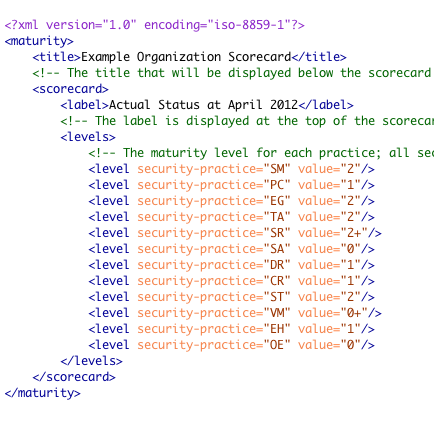
The XML is a very similar structure as used for the roadmap charts, but only one set of data are required.
Like the roadmap files, Maturity Level information can be 0, 1, 2 and 3 or where there is additional assurances in place beyond those indicated by the Level, the “+” symbol can be used so 0+, 1+ and 2+ are also allowed.
Download the files
Download the archive of files.
The archive includes the an example XML file and the US English SAMM base XML file. Remember the latter should normally be downloaded from the SAMM download page. Using a web browser, open the example SVG file from the directory, for example:
file:///e:/path/samm/scorecard/scorecard-ex1.svg
Create your own chart
Edit and save the XML file. Then check the file is well-formed. The simplest method is to use the W3C Markup Validation Service to upload the file or directly input the file content. If your data contains confidential information, you may want to undertake this check locally instead.
Then once the file has passed the previous check, test the XML structure against the XML Schema Definition (XSD) provided in the download link above:
SAMM-1.0-scorecard-0.2.xsd
Take a tool which can undertake XSLT conversions, and apply SAMM-1.0-scorecard-0.2-en_US.xsl to your XML file. An SVG file should be created. That’s all there is to it.
Again if you don’t want to use XML and XSLT, you can just edit the SVG files directly using some sort of text editor.
Mapping SAMM to ISO/IEC 27034
Posted by Colin Watson in Discussion on April 7th, 2012
ISO/IEC 27034 (Application Security), which can be purchased from International Organization for Standardization (ISO) and national standards bodies, is designed to help organisations build security throughout the life cycle of applications.
There is a preview of the contents and first few pages of Part 1 on the IEC website. Part 1 presents an overview of application security and introduces definitions, concepts, principles and processes involved in application security.
The contents listing for Annex A of ISO/IEC 27034:2011 Part 1 mentions a mapping to the Microsoft Security Development Lifecycle (SDL), and in the section describing the standard’s purpose, it refers to the need to map existing software development processes to ISO/IEC 27034:
Annex A (informative) provides an example illustrating how an existing software development process can be mapped to some of the components and processes of ISO/IEC 27034. Generally speaking, an organization using any development life cycle should perform a mapping such as the one described in Annex A, and add whatever missing components or processes are needed for compliance with ISO/IEC 27034.
The contents for Part 1 shows the SDL is compared with an Organization Normative Framework (ONF) made up from ideal application security related processes and resources:
- Business context
- Regulatory context
- Application specifications repository
- Technological context
- Roles, responsibilities and qualifications
- Organisation application security control (ASC) library
- Application security life cycle reference model
This is very useful but I wondered how a comparison with Open SAMM might look. I have therefore created the table below indicating how the processes and resources mapped to SDL relate to the 12 security practices defined in Open SAMM. The large diamond symbol is used to indicated where an Open SAMM practice has a very close relationship with a topic within ISO/IEC 27034 and a smaller diamond for weaker relationships.
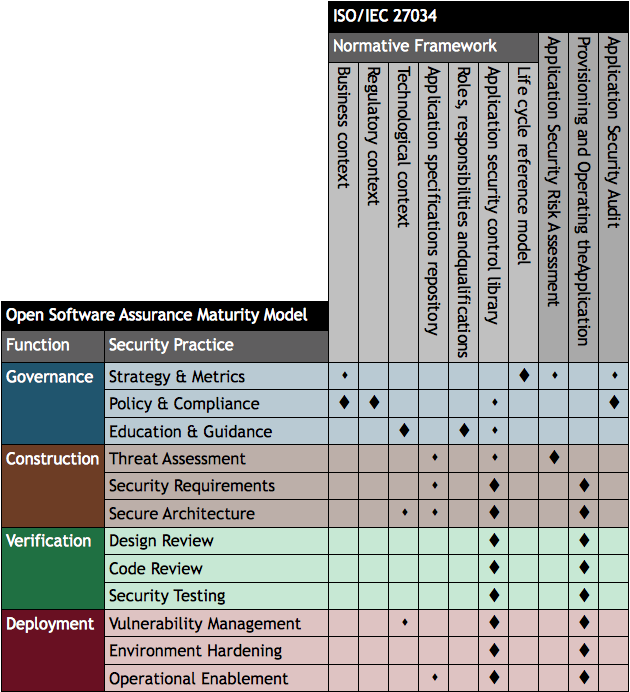
The ISO/IEC 27034 “life cycle reference model” appears to be most closely aligned with the idea of an organisation-specific “software assurance programme” in SAMM combined with a risk-based approach to applying security to different applications, and within sub-parts of application systems.
We can also see the SAMM construction, verification and deployment practices primarily relate to the ISO/IEC 27034 application security control library used for the overall organisation and individual applications, as well as the actual use of the framework during acquisition/development, deployment and operation of (provisioning and operating) the application.
SAMM is available to download free of charge, and can also be purchased at-cost as a colour soft cover book.
Mapping SAMM to Security Automation
Posted by Colin Watson in Discussion on March 25th, 2012
The presentation by Richard Struse (US Department of Homeland Security) and Steve Christey (Mitre) of Risk Analysis and Measurement with CWRAF (PDF) at the IT Security Automation Conference in October 2011 illustrates how software security automation enumerations and protocols map to SAMM’s construction, verification and deployment security practices. The specifications highlighted in the presentation’s final slide are:
- Common Attack Pattern Enumeration and Classification (CAPEC)
- Common Weakness Enumeration (CWE)
- Common Weakness Risk Analysis Framework (CWRAF)
- Common Weakness Scoring System (CWSS)
- CWE Coverage Claims Representation (CCR)
- Security Content Automation Protocol (SCAP)
I have summarised the slide in the table below.
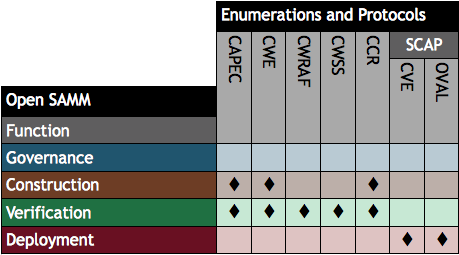
For further security registries, description languages and standardised processes see the Making Security Measurable website. Risk Analysis and Measurement with CWRAF is being presented at AppSec DC 2012 in April.
Todo en español
Posted by Pravir Chandra in Discussion, Releases on July 26th, 2011
 Thanks to the team led by Juan Carlos Calderon, we have a complete translation of the SAMM 1.0 into Spanish available now on the downloads page. This would not have been possible without the translation work performed by the team of Francisco Aldrete, Luis Martínez Bacha, Miguel Pérez-Milicua, Alvaro Muñoz, and Aldo Salas.
Thanks to the team led by Juan Carlos Calderon, we have a complete translation of the SAMM 1.0 into Spanish available now on the downloads page. This would not have been possible without the translation work performed by the team of Francisco Aldrete, Luis Martínez Bacha, Miguel Pérez-Milicua, Alvaro Muñoz, and Aldo Salas.
Also, Joaquin Crespo from the Spain contingent of OWASP contributed a full translation of the OpenSAMM 1.0 overview presentation. That’s also available on the downloads page.
To everyone involved in the translation work, I would like to personally extend my thanks and gratitude to each one of you for this valuable contribution to the project. If anyone reading this would like to lead a translation to your language of choice, just post a message to the SAMM mailing list and we’d be glad to help you get started.
OpenSAMM in eBook Format
Posted by Colin Watson in Discussion on April 1st, 2011
The OpenSAMM 1.0 English XML source file has been converted into an eBook format by Paweł Krawczyk.
You can read more about the file and download it on IPsec.pl at http://ipsec.pl/node/967
BSIMM activities mapped to SAMM
Posted by Pravir Chandra in Changes, Discussion on March 3rd, 2011
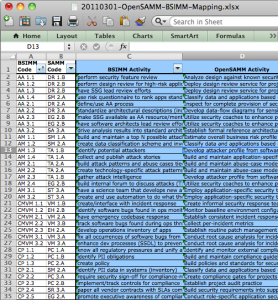 For the impatient, click here to download the mapping spreadsheet. For those still reading… Firstly, many thanks to the OWASP community for hosting the fantastic OWASP Summit 2011 in Lisbon, Portugal a few weeks back. This was a fantastic forum for us to hold OpenSAMM working sessions to discuss experiences and potential improvements to the model. Over the course of the week, we were able to build up a list of additions/changes we’d like to make in the next release, but I’ll cover those in more detail under separate cover.
For the impatient, click here to download the mapping spreadsheet. For those still reading… Firstly, many thanks to the OWASP community for hosting the fantastic OWASP Summit 2011 in Lisbon, Portugal a few weeks back. This was a fantastic forum for us to hold OpenSAMM working sessions to discuss experiences and potential improvements to the model. Over the course of the week, we were able to build up a list of additions/changes we’d like to make in the next release, but I’ll cover those in more detail under separate cover.
The main thing I want to share now is an activity-level mapping of the ~110 BSIMM2 activities to the corresponding 72 activities in SAMM. Obviously, this means that in some cases, more than one BSIMM activity may be mapped to a single SAMM activity. That being said, the overlap spots seem to make sense when we (the ~10 people that worked on it) looked at them in detail. Don’t take our word for it, though, please do review and send any feedback (mailing list or just comment below). And before you ask, yes, you probably will have to go read the respective BSIMM and SAMM activity descriptions in order to see the linkage for some of them (given the occasionally imprecise nature of written language, it’s not always obvious from the activity names alone).
It’s worth noting that we did leave two BSIMM activities unmapped. They are SM 3.2 “run external marketing program” and T 3.3 “host external software security events”. Based on the experience of the working group participants, these activities did not appear to directly improve an organization’s software assurance posture, rather, they appeared to be evidence that the organization was using its (presumably mature) software assurance posture to bolster its public perception or generate additional value in the business. Again, this is totally up for debate if anyone has an argument the other way, so please do share your thoughts.
Last, but certainly not least, I’d like to thank all the people at the Summit for the detailed and thoughtful conversations about using SAMM and about what we can do to make it even better. Specifically, those that contributed and helped review this mapping (in no particular order):
- Colin Watson
- Seba Deleersnyder
- Steven van der Baan
- Bart De Win
- Justin Clarke
- Dan Cornell
- Sherif Koussa
- Brian Chess
OpenSAMM Overview Presentation in French
Posted by Pravir Chandra in Discussion on October 20th, 2010
 Thanks to Hubert Grégoire and Sebastien Gioria, we now have a French translation of the OpenSAMM 1.0 Overview presentation available for download. You can get it from the download tab or there is a direct link here.
Thanks to Hubert Grégoire and Sebastien Gioria, we now have a French translation of the OpenSAMM 1.0 Overview presentation available for download. You can get it from the download tab or there is a direct link here.
If anyone else has translated the presentation to other languages for local chapter presentations, please feel free to send them to me (or the mailing list) and we’ll get them posted for all to access.
Roadmap Chart Generation – Part 3 of 3
Posted by Colin Watson in Discussion, Releases on September 27th, 2010
Yesterday Part 2 described how to create and validate the source roadmap data files. In this post, transforming the data files into the final SVG format we saw in Part 1 will be described.
The great thing about having data in XML is the ability to translate it easily into another format using Extensible Stylesheet Language Transformations (XSLT).
Transformation
Download the archive of files.
With Brenda’s assistance we now have an XSLT file which can be used to translate a valid and well-formed SAMM Roadmap source data file into a valid SVG file. You need the two XSL files included in the archive download linked above:
SAMM-1.0-roadmap-0.6-en_US.xsl
SAMM-1.0-utilities-0.1.xsl
You also need the base US English XML file (version 0.3) for SAMM v1.0 and your XML data files. The archive includes the two example XML files from Part 1 (again) and the US English SAMM base XML file. Remember the latter should normally be downloaded from the SAMM download page. Place all the files in a new directory.
Take a tool which can undertake XSLT conversions, and apply SAMM-1.0-roadmap-0.6-en_US.xsl to your XML file or one of the examples. An SVG file should be created.
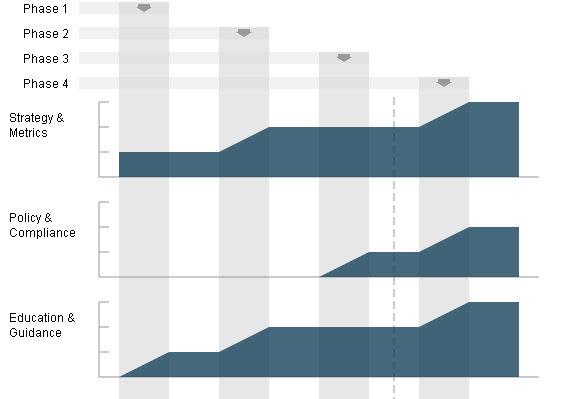
Partial screen capture (as a JPEG) of a generated SVG SAMM Roadmap Chart
And that’s it. Alter your XML files to see the effect on the generated SVG charts.
If you don’t want to use XML and XSLT, you can of course just edit the SVG files directly using some sort of text editor.
Next
I hope to spend some time creating SVG charts for the SAMM scorecard charts sometime soon.