Archive for category Discussion
Where to find the latest SAMM release?
Posted by Seba Deleersnyder in Discussion on September 11th, 2019
After OpenSAMM v1.0 was donated to OWASP, it evolved into OWASP SAMM, which is further developed and maintained by the OWASP SAMM project team.
You can find the latest downloads and releases at https://owaspsamm.org
OWASP SAMM v1.5 released
Posted by Seba Deleersnyder in Discussion on April 13th, 2017
OWASP released OWASP SAMM v1.5!
OWASP SAMM v1.5 improves the granularity of scoring, allowing partial credit for achieving maturity benchmarks. This coupled with the matching scoring system, makes it easy to see maturity improvements from projects and initiatives on a dashboard. SAMM project co-lead Brian Glas notes, “One of the main benefits of the updated scoring model is that you can visibly see improvement to your maturity score on the dashboard as initiatives are completed. This can go a long way in building support for your Application Security Program.”
Version 1.5 has enhanced explanations of the maturity model with worksheets and guidance containing example case studies which allows organizations not only understand where they are, but to understand what has worked (and hasn’t) for others in similar scenarios. This is a continuing effort with more improvements expected in v2.0. Join us to create the next release at the SAMM Working Sessions at the upcoming OWASP Summit near London in June 2017 (details: http://owaspsummit.org/Working-Sessions/OwaspSAMM/)
To learn more, visit https://www.owasp.org/index.php/SAMM
To read the press release, visit http://www.prnewswire.com/news-releases/owasp-samm-v15-helps-organizations-improve-their-security-posture-300439237.html
OWASP SAMMv1.1 available
Posted by Seba Deleersnyder in Discussion on April 20th, 2016
Dear,
The new OWASP SAMM v1.1 is published by the OWASP SAMM project on 16-Mar 2016.
See the press release here.
All SAMM downloads are available from the OWASP wiki pages.
Kind regards,
Seba
OpenSAMM Summit Dublin – Outcome
Posted by Seba Deleersnyder in Changes, Discussion, Releases on April 5th, 2015
Last week we had our first OpenSAMM Summit in Dublin on 27-28 March.
Full agenda for the User and Project Day are available here:
https://www.owasp.org/index.php/OWASP_SAMM_Summit_2015
We had about 30 people gathering on the User day, with presentations (now available online (linked in the agenda page), a short OpenSAMM training (slides also available) and 2 great round tables to discuss OpenSAMM experiences.
On Friday evening most attendees came together in the centre of Dublin for the social event in the Cocktail / Winter Garden at Fade Street Social. Great food and lots of Guinness!
The Project day on Saturday was packed with constructive discussions and decisions on the content and release of v1.1 of OpenSAMM and the evolution of the tooling & guidance to support is. More details on the OpenSAMM Benchmark initiative – which was announce during the User day – were presented and debated together with a timeline for the release of the first data set (expect this by September 2015).
The User day meeting notes – together with the list of actions – are available here:
https://docs.google.com/document/d/1pC4har75olF1WPZaqRfXFG9T3SS_qoEUvHkEynE0iTI
The final release of OpenSAMM v1.1 will be done in the coming weeks. The core model will be split of the full document. Some nomenclature changes were decided to better cover the underlying OpenSAMM security activities. The how-to, templates, toolbox and quick-start guide will be released separately and will have their own versioning. The existing mappings from other frameworks will also be updated and now includes a mapping on PCI DSS v3.
Overall feedback scores from the survey on the summit were great. Overall score was 93.3 % ! Detailed scores and lessons learned have been captured here:
https://docs.google.com/document/d/1tHdZFjsNwqhD1iYXBQyrgtBLLI_sTRn_kx8HSyKqNEY
I want to thank all participants, my project co-leaders and the supporting sponsors for making this summit a big success!
I will finish with the following quote: “The SAMM summit provided an opportunity to breathe new life into a framework that I use to facilitate my day-to-day work and support my customers.” Bruce C Jenkins, Fortify Security Lead, Hewlett-Packard Company
Stay tuned for the release of OpenSAMM v1.1 and hope to see you at one of our next OpenSAMM summits!
Seba
OpenSAMM Project Team
SAMM Summit in Dublin
Posted by Colin Watson in Discussion on March 8th, 2015
Join the OWASP SAMM Summit 2015 in Dublin on 27th-28th March. The agenda is:
Friday 27-March – User Day:
- Talks
- Training
- Topic roundtables
Saturday 28-March – Project Day:
- Publish SAMM v1.1
- Workshops
- Road map
Confirmed speakers, trainers and round sessions and registration information are detailed in the summit microsite.
SAMM Workshop Next Week in Hamburg
Posted by Colin Watson in Discussion on August 14th, 2013
Further to the previous announcement, the schedule for the SAMM workshop at AppSec EU in Hamburg next week has been published.
During AppSec conferences, the SAMM project team will organise workshops for you to influence the direction SAMM evolves. This is also an excellent opportunity to exchange experiences with your peers. Similar workshops will be organised in New York (USA) and Lima (Peru) in the coming months.
Next week on Wednesday the project leaders are holding the first of these OpenSAMM workshops at AppSec.eu in Hamburg:
- Location: Alster room in the Scandic Hotel, Hamburg, Germany
- Time: Wednesday August 21, 2013 1:00pm – 4:00pm
The agenda is:
- Introduction / getting to know each other – 10 mins
- Project status and goals – 10 mins
- OpenSAMM inventory of tools and templates – 20 mins
- Case studies / sharing experiences – 40 mins
- What do we need (thinking about improvements, can be anything ranging from translations over tools to model improvements) – 40 mins
- What do we need first (prioritization) – 30 mins
- Call for involvement (responsibilities), identity teams for specific topics – 15 mins
- Rough planning for the future – 15 mins
If you plan to come, can you add your name to the online meeting document.
If you would like to cover other topics, don’t hesitate to contact Seba Deleersnyder or Bart De Win.
Hopefully there will be a gotomeeting call to allow for remote participation; please let Seba or Bart know if you would like to participate remotely.
OpenSAMM Adopters
Posted by Colin Watson in Discussion on August 13th, 2013
The SAMM project leaders have started an OpenSAMM Adopters page at:
https://www.owasp.org/index.php/OpenSAMM_Adopters
If you use SAMM or you know of an organisation using SAMM that is willing to share this information publicly, please add details to the following page, or forward to Seba Deleersnyder if you do not have, or do not want want, an OWASP wiki account.
- Organization name
- Contact
- Role
- Organization type
- Region
- Optional testimonial
SAMM workshops at AppSec EU and AppSec USA
Posted by Colin Watson in Discussion on August 2nd, 2013
If you plan on attending http://appsec.eu or http://appsecusa.org/ be sure to get involved in the SAMM workshops (scheduled on Aug-21 and Nov-20). In Hamburg, the SAMM workshop will be on Wednesday afternoon 21-Aug, one day prior to the conference.
If you plan to attend the workshop: let us know via the project mailing list.
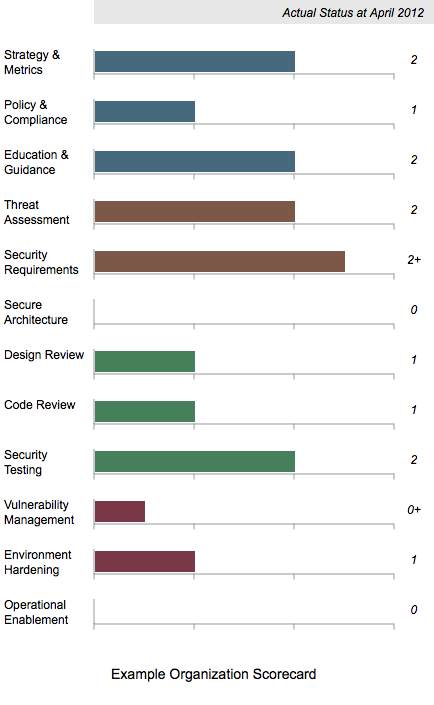
Scorecard Chart Generation
Posted by Colin Watson in Discussion on August 7th, 2012
Building on the work undertaken with Brena Larcom to create SAMM roadmap charts (Part 1, Part 2 and Part 3), I have developed a similar process for single point in time scorecards.
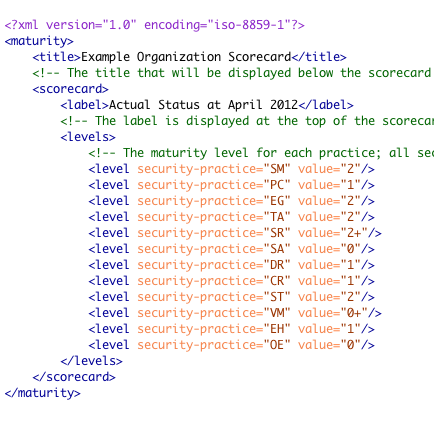
The XML is a very similar structure as used for the roadmap charts, but only one set of data are required.
Like the roadmap files, Maturity Level information can be 0, 1, 2 and 3 or where there is additional assurances in place beyond those indicated by the Level, the “+” symbol can be used so 0+, 1+ and 2+ are also allowed.
Download the files
Download the archive of files.
The archive includes the an example XML file and the US English SAMM base XML file. Remember the latter should normally be downloaded from the SAMM download page. Using a web browser, open the example SVG file from the directory, for example:
file:///e:/path/samm/scorecard/scorecard-ex1.svg
Create your own chart
Edit and save the XML file. Then check the file is well-formed. The simplest method is to use the W3C Markup Validation Service to upload the file or directly input the file content. If your data contains confidential information, you may want to undertake this check locally instead.
Then once the file has passed the previous check, test the XML structure against the XML Schema Definition (XSD) provided in the download link above:
SAMM-1.0-scorecard-0.2.xsd
Take a tool which can undertake XSLT conversions, and apply SAMM-1.0-scorecard-0.2-en_US.xsl to your XML file. An SVG file should be created. That’s all there is to it.
Again if you don’t want to use XML and XSLT, you can just edit the SVG files directly using some sort of text editor.
Mapping SAMM to ISO/IEC 27034
Posted by Colin Watson in Discussion on April 7th, 2012
ISO/IEC 27034 (Application Security), which can be purchased from International Organization for Standardization (ISO) and national standards bodies, is designed to help organisations build security throughout the life cycle of applications.
There is a preview of the contents and first few pages of Part 1 on the IEC website. Part 1 presents an overview of application security and introduces definitions, concepts, principles and processes involved in application security.
The contents listing for Annex A of ISO/IEC 27034:2011 Part 1 mentions a mapping to the Microsoft Security Development Lifecycle (SDL), and in the section describing the standard’s purpose, it refers to the need to map existing software development processes to ISO/IEC 27034:
Annex A (informative) provides an example illustrating how an existing software development process can be mapped to some of the components and processes of ISO/IEC 27034. Generally speaking, an organization using any development life cycle should perform a mapping such as the one described in Annex A, and add whatever missing components or processes are needed for compliance with ISO/IEC 27034.
The contents for Part 1 shows the SDL is compared with an Organization Normative Framework (ONF) made up from ideal application security related processes and resources:
- Business context
- Regulatory context
- Application specifications repository
- Technological context
- Roles, responsibilities and qualifications
- Organisation application security control (ASC) library
- Application security life cycle reference model
This is very useful but I wondered how a comparison with Open SAMM might look. I have therefore created the table below indicating how the processes and resources mapped to SDL relate to the 12 security practices defined in Open SAMM. The large diamond symbol is used to indicated where an Open SAMM practice has a very close relationship with a topic within ISO/IEC 27034 and a smaller diamond for weaker relationships.
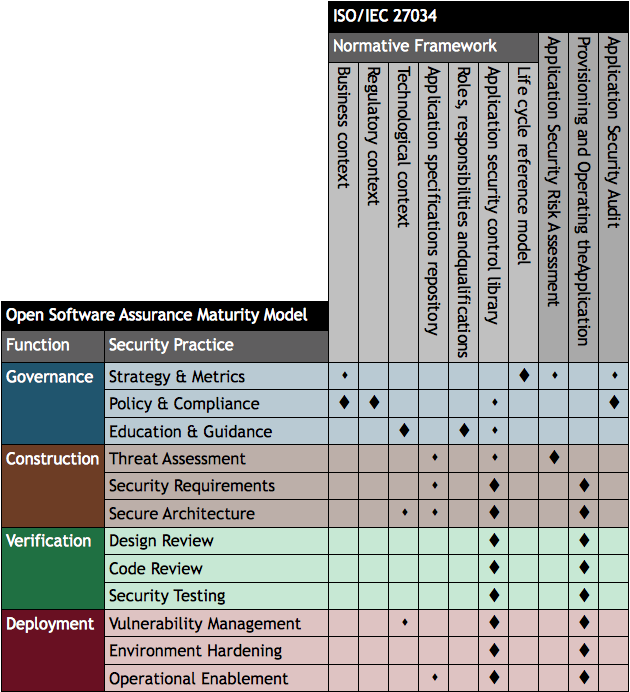
The ISO/IEC 27034 “life cycle reference model” appears to be most closely aligned with the idea of an organisation-specific “software assurance programme” in SAMM combined with a risk-based approach to applying security to different applications, and within sub-parts of application systems.
We can also see the SAMM construction, verification and deployment practices primarily relate to the ISO/IEC 27034 application security control library used for the overall organisation and individual applications, as well as the actual use of the framework during acquisition/development, deployment and operation of (provisioning and operating) the application.
SAMM is available to download free of charge, and can also be purchased at-cost as a colour soft cover book.